TL;DR
- Stablecoins are critical to crypto markets, but come with distinct security risks depending on how they are issued and managed.
- Centralized stablecoins carry custodial and regulatory risks, whereas decentralized stablecoins can face smart contract and oracle vulnerabilities.
- Hackers exploit stablecoins through phishing, contract exploits, rug pulls, and fake tokens — often with significant market consequences.
- Chainalysis Hexagate helps users and platforms detect and respond to suspicious activity involving stablecoins in real time.
Stablecoins are digital assets designed to maintain a fixed or stable value, typically pegged to fiat currencies like the U.S. dollar. They play a central role in the crypto ecosystem, powering decentralized finance (DeFi) protocols, enabling payments and remittances, and facilitating on-chain liquidity. However, the growing use of stablecoins has also made them a prime target for bad actors.
Chainalysis Hexagate helps mitigate these risks by enabling real-time monitoring of stablecoin balances, transactional behavior, and contract interactions. As stablecoin adoption grows, visibility into these crypto assets becomes crucial to safeguarding users and trading platforms.
Keep reading to learn more about the following topics:
- Why stablecoins are attractive but vulnerable
- Types of stablecoins and their security implications
- Common stablecoin security risks
- Incidents involving stablecoin exploits
- How stablecoins pose risks to financial systems
- How Chainalysis Hexagate helps monitor stablecoin risk
- Best practices for stablecoin users and platforms
Why stablecoins are attractive but vulnerable
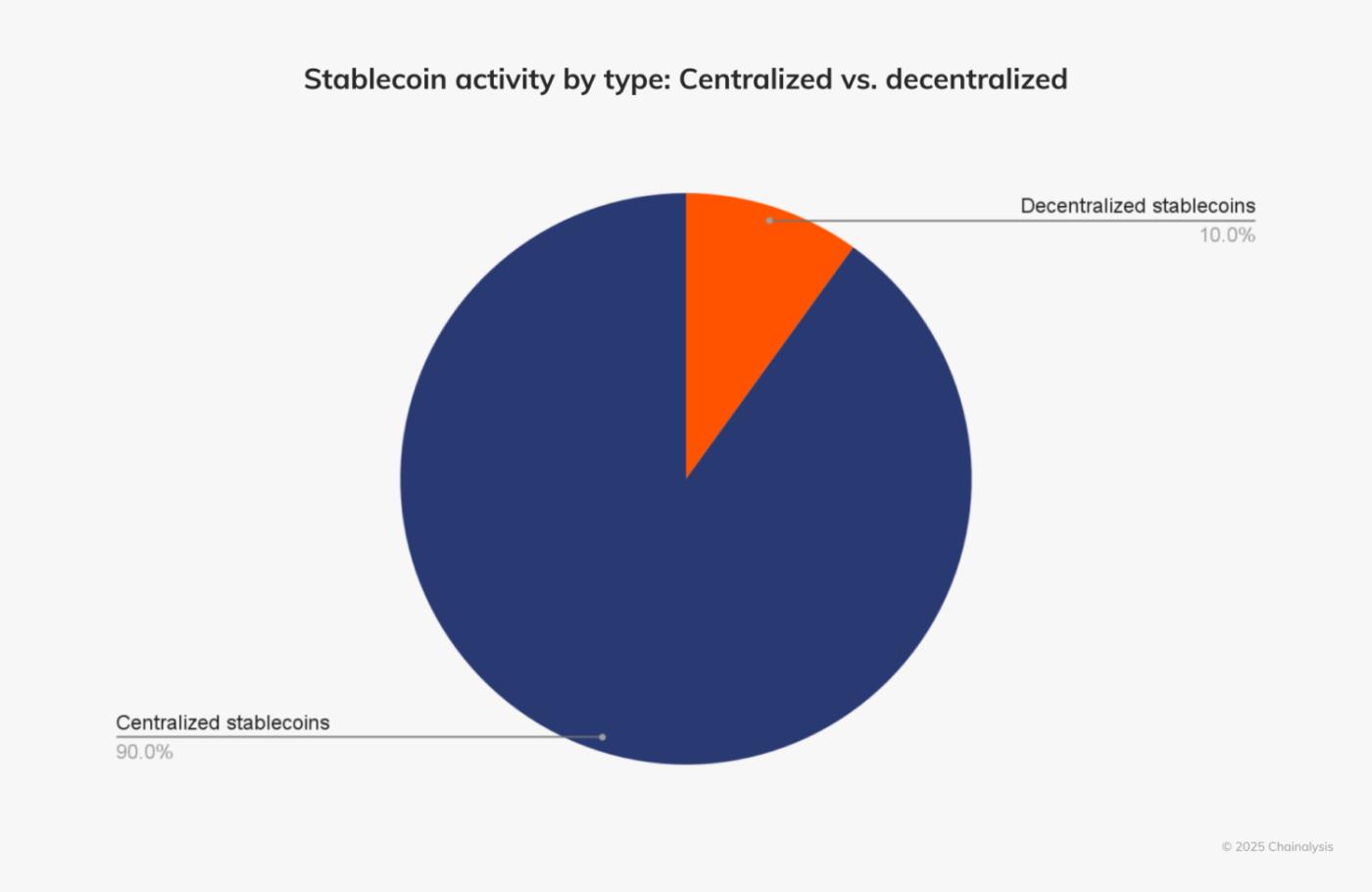
Stablecoins are designed to offer low volatility and fast settlement, making them indispensable across centralized exchanges (CEXs), DeFi, and global payment systems. As we see in the chart below, which shows stablecoin activity by type, centralized stablecoins are significantly more popular than decentralized stablecoins, accounting for 90% of the current share of stablecoin activity.
That same utility, however, makes stablecoins targets for cybercriminals looking to exploit users, infrastructure, and protocols.
Types of stablecoins and their security implications
Centralized stablecoins
Centralized stablecoins like USDC and USDT are backed by reserves held by their issuers, typically consisting of cash, short-term government securities, or other low-risk assets. While this backing model provides transparency and regulatory compliance, it introduces significant custodial risk — users must trust the issuer to maintain adequate reserve assets and operate with integrity.
These stablecoins also face regulatory exposure and centralized points of failure, as government actions or operational disruptions at the issuing company can affect the entire token supply and its availability across global markets.
Currently, the majority of centralized stablecoin activity occurs in DeFi and on CEXs.

Decentralized stablecoins
Decentralized stablecoins such as DAI and crvUSD are backed by crypto collateral or governed by algorithmic mechanisms, removing the need for traditional custodial relationships. However, this decentralized approach introduces different security challenges — particularly smart contract vulnerabilities that can be exploited by attackers to manipulate token issuance or drain collateral pools.
Decentralized stablecoins also rely heavily on oracles and liquidation mechanisms to maintain their pegs, creating additional attack surfaces where price manipulation or oracle failures can destabilize the entire stablecoin ecosystem.
Currently, the majority of decentralized stablecoin activity occurs with mining and in DeFi.

Common stablecoin security risks
The diverse attack vectors targeting stablecoins reflect their central role in crypto infrastructure. Understanding these risks is essential for users and platforms seeking to protect their assets.
Smart contract exploits
Vulnerabilities in DeFi protocols that use or issue stablecoins represent one of the most technically sophisticated threat vectors. Attackers identify flaws in smart contract code — such as reentrancy bugs, logic errors, or inadequate access controls — to drain funds or manipulate token issuance. These exploits can affect both the stablecoin protocol itself and the broader DeFi ecosystem that relies on these tokens for liquidity and collateral.
Custodial breaches
Centralized stablecoins face risks associated with the storage of reserves and issuance controls. If hackers compromise the infrastructure of stablecoin issuers, they may gain access to reserve funds or the ability to mint unauthorized tokens. These breaches can undermine confidence in the stablecoin’s backing and potentially trigger market-wide instability.
Phishing and social engineering
Attackers frequently target individual users through sophisticated phishing campaigns designed to steal private keys or trick users into authorizing malicious transactions. These attacks often impersonate legitimate stablecoin platforms, wallets, or DeFi protocols to gain user trust before stealing funds.
Rug pulls and exit scams
Bad actors create fraudulent stablecoins or copycat tokens designed to appear legitimate before disappearing with investor funds. These schemes often involve fake tokenomics, misleading marketing, and artificial price manipulation to attract victims before the inevitable exit.
Flash loan attacks
These complex exploits use uncollateralized loans to manipulate DeFi markets and destabilize stablecoin price pegs. Attackers borrow large amounts of capital, execute price manipulation across multiple protocols, and profit from arbitrage opportunities — all within a single transaction block.
Impersonation and fake stablecoins
Criminals create tokens with names and symbols similar to legitimate stablecoins to confuse users. These fake tokens may appear in wallet interfaces or on decentralized exchanges, tricking users into accepting worthless assets in exchange for real value.
Incidents involving stablecoin exploits
Recent history provides examples of how stablecoin vulnerabilities can cascade through the crypto ecosystem. The collapse of TerraUSD (UST) in May 2022 demonstrated how algorithmic stablecoins can lose their peg during market stress, wiping out over $60 billion in value and triggering broader market contagion. The incident highlighted the risks of experimental tokenomics and insufficient collateralization mechanisms.
DeFi protocols utilizing established stablecoins like USDC and DAI have also faced significant exploits. The Euler Finance hack in March 2023 resulted in approximately $197 million in losses, much of which involved stablecoins that were drained from the protocol’s lending pools. Similarly, the Curve Finance exploit in July 2023 put hundreds of millions in stablecoin liquidity at risk due to a vulnerability in the protocol’s smart contracts.
These incidents demonstrate how stablecoin-related attacks extend far beyond individual token protocols. When major stablecoins lose their peg or face liquidity crises, the effects ripple through DeFi protocols, centralized exchanges, and traditional financial institutions that have begun integrating these assets into their operations.
The role of blockchain visibility becomes crucial in analyzing and responding to these events. Real-time monitoring allows stakeholders to track fund flows, identify suspicious patterns, and coordinate response efforts across platforms. Without this visibility, the full scope and timeline of attacks often remain unclear for days or weeks after the initial exploit.
How stablecoins pose risks to financial systems
The integration of stablecoins into traditional finance creates new systemic risk vectors that extend beyond individual protocols or platforms. DeFi protocols have become heavily reliant on stablecoins for liquidity provision, with many platforms holding billions of dollars in these assets. A failure of a major stablecoin could trigger cascading liquidations across interconnected protocols, potentially freezing large portions of the DeFi ecosystem.
The potential for contagion from a major stablecoin failure poses particular concerns for institutional adoption. As traditional financial institutions increasingly hold or transact in stablecoins, their exposure to crypto-specific risks grows. A significant depegging event could force institutions to realize losses, potentially affecting their ability to serve traditional banking customers.
Regulatory scrutiny has intensified around stablecoins’ role in potential sanctions evasion and capital flight. The pseudonymous nature of blockchain transactions, combined with stablecoins’ stability and global accessibility, makes them attractive for actors seeking to move value across borders without traditional banking oversight. This has led to increased geopolitical tensions around stablecoin regulation and usage.
Bad actors leverage stablecoins for money laundering and obfuscating illicit fund flows precisely because of their stability and widespread acceptance. Unlike volatile cryptocurrencies, stablecoins allow criminals to preserve value while moving funds through complex transaction patterns designed to obscure their origins. The challenge for compliance teams lies in distinguishing legitimate privacy-seeking behavior from genuine criminal activity.
How Chainalysis Hexagate helps monitor stablecoin risk
Chainalysis Hexagate provides comprehensive visibility into stablecoin ecosystems through real-time monitoring of reserves, stablecoin involvement of hacks, de-pegs on exchanges, privileged activity, involvement of hacks, and more. The platform tracks stablecoin movements across multiple blockchains, enabling users to identify risks and suspicious activity patterns that might indicate impending exploits or ongoing attacks.
The solution’s smart contract monitoring capabilities help detect unusual interactions with stablecoin protocols, such as large withdrawals, unexpected minting events, or transactions involving known malicious addresses. By maintaining updated intelligence on emerging threats, Hexagate can alert users to potential risks before they materialize into significant losses.
Best practices for stablecoin users and platforms
Individual stablecoin users should prioritize verifying token contracts before conducting transactions, as fake stablecoins frequently impersonate legitimate tokens through similar names or symbols. Always cross-reference contract addresses through official channels rather than relying on third-party listings. Implementing strong wallet hygiene practices — including using hardware wallets for significant holdings and enabling multi-factor authentication — provides additional security layers. Users should also remain vigilant against phishing attempts, particularly those involving urgent requests to authorize transactions or provide private keys.
Institutions handling stablecoins should conduct thorough smart contract audits before integrating new stablecoin protocols or major updates to existing ones. Real-time monitoring systems that track unusual transaction patterns, large withdrawals, or interactions with suspicious addresses help identify potential threats before they escalate. Compliance with anti-money laundering (AML) regulatory frameworks requires ongoing transaction screening and reporting mechanisms tailored to stablecoin-specific risks.
The importance of education and cross-industry collaboration cannot be overstated in reducing overall ecosystem risk. Sharing threat intelligence, coordinating response efforts during major incidents, and establishing industry standards for stablecoin security helps protect the entire ecosystem rather than individual platforms operating in isolation.
Book a demo of Chainalysis Hexagate’s security solution here.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.
The post The Security Risks of Stablecoins: How Hackers Exploit Centralized and Decentralized Issuers appeared first on Chainalysis.





